How to add service or port by Firewall on centos 7 - Linux Mining
Firewalld is a front-end controller for iptables that implements persistent network traffic rules. It provides a command-line and a graphical interface.
Comparison of Firewalld and iptables:
1. Firewalld can dynamically modify a single rule or manage the ruleset, allowing updates to the rules without breaking existing sessions and connections. Whereas in iptables, after modifying the rules, it must be fully refreshed to take effect.
2. Firewalld uses regions and services instead of chained rules.
3. Firewalld default is rejected, you need to set it later to release. And iptables is allowed by default, and you need to reject it to limit it.
4. Firewalld itself does not have the function of a firewall, but like iptables need to be implemented through the kernel’s Netfilter. That is to say, Firewalld is the same as iptables, their role is to maintain the rules, and the real use of the rules is the kernel’s Netfilter. Only the results of firewalld and iptables and the method of use are different!
Firewalld is a wrapper for iptables that makes it easier to manage iptables rules. It is not a replacement for iptables, although the iptables command can still be used for firewalld, it is recommended to use only the firewalld command for firewalld.
Initialization area:
block: Any incoming network packets will be blocked;
work: Believe that other computers on the network will not harm your computer;
home: Tell that other computer on the network will not harm your computer;
Public area (public): Do not trust any computer on the network, only choose to accept incoming network connections.
Isolated Area (DMZ): Also known as the demilitarized area, a layer of the network between the internal and external networks acts as a buffer. For isolated areas, only choose to accept incoming network connections.
Trusted zone (trusted): All network connections are acceptable.
drop: Any incoming network connection is rejected.
internal: Trust other computers on the network without harming your computer. Only choose to accept incoming network connections.
external: Do not trust other computers on the network and would harm your computer. Only choose to accept incoming network connections.
The default area of firewalld is public.
RHEL 8 / CentOS 8 open HTTP port 80 and HTTPS port 443 step by step instructions
- Check the status of your firewall.
# firewall-cmd --state running
Retrieve your currently active zones. Take a note of the zone within which you wish to open ports 80 and 443:
# firewall-cmd --get-active-zones libvirt interfaces: virbr0 public interfaces: enp0s3- Open port 80 and port 443 port.
The port 80 and port 443 ports are listed with Firewalld as
httpandhttpsservices. To temporarily open both ports execute:# firewall-cmd --zone=public --add-service=http # firewall-cmd --zone=public --add-service=https
Note, the above
firewaldcommands will open HTTP and HTTPS port only temporarily. - Open port 80 and port 443 port permanently. Execute the below commands to open both ports permanently, hence, make the settings persistent after reboot:
# firewall-cmd --zone=public --permanent --add-service=http # firewall-cmd --zone=public --permanent --add-service=https # firewall-cmd --reload
- Check for open ports/services. The services with permanently open ports are listed on line starting with
services::# firewall-cmd --list-all public (active) target: default icmp-block-inversion: no interfaces: enp0s3 sources: services: cockpit dhcpv6-client http https ssh ports: protocols: masquerade: no forward-ports: source-ports: icmp-blocks: rich rules: - In case you need to close the previously open HTTP port 80 and HTTPS port 443 execute:
# firewall-cmd --zone=public --permanent --remove-service=http # firewall-cmd --zone=public --permanent --remove-service=https # firewall-cmd --reload
First install firewall on your system :
yum install firewalld -yNow start & enable firewall :
systemctl start firewalld
systemctl enable firewalld
systemctl status firewalld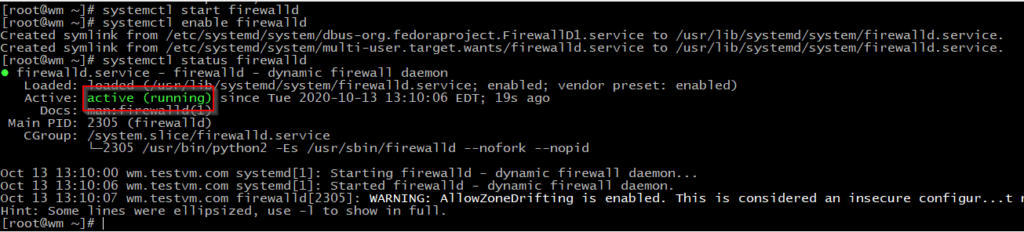
Now see how many zones in your system & who is your default zone :
firewall-cmd --get-zones
firewall-cmd --get-default-zoneYour default zone must be public if not then set default zone to public or your system may not work properly :
firewall-cmd --set-default-zone=publicNow see the permanent list of all services & ports on your public zone :
firewall-cmd --permanent --zone=public --list-all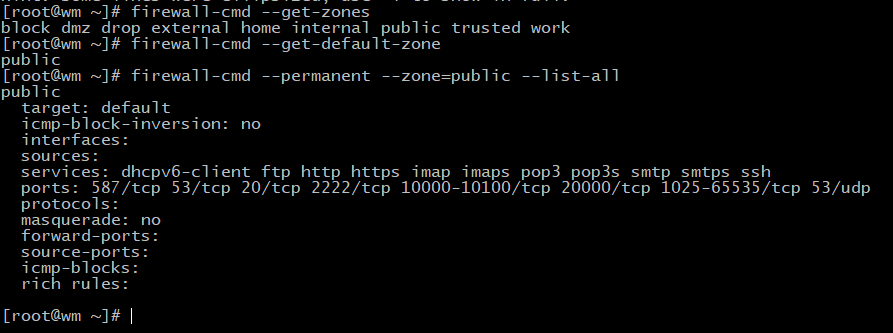
If you need to add any service on your public zone then you can add like this :
firewall-cmd --permanent --zone=public --add-service=http
firewall-cmd --permanent --zone=public --list-services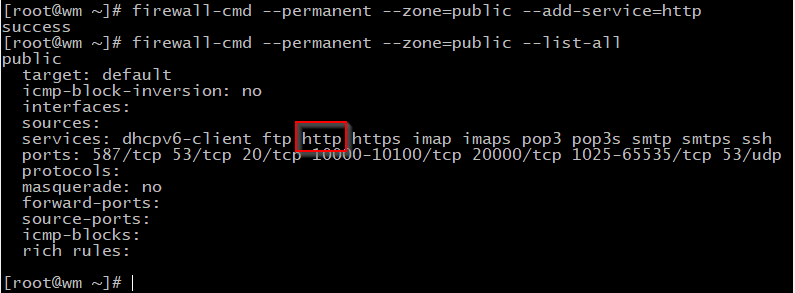
If you want to remove any service from your public zone you can do like this :
firewall-cmd --permanent --zone=public --remove-service=httpNow add a port to public zone & remove it if you need by this command :
firewall-cmd --permanent --zone=public --add-port=2222/tcp
firewall-cmd --zone=public --list-ports
firewall-cmd --permanent --zone=public --remove-port=25/tcp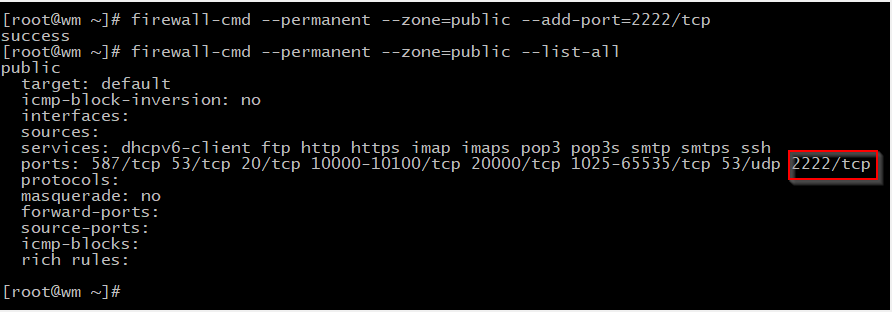
Thank you for reading this article.
Không có nhận xét nào:
Đăng nhận xét